RFC2617 section 1.2 defines a Protection Space as the domain over which credentials can be automatically applied. If a prior request has been authorized, the same credentials may be reused for all other requests within that protection space for a period of time determined by the authentication scheme, parameters, and/or user preference. Just reverse all the settings that are made above and to those who are still confused on how it all should look like at the other end, below are a couple of screenshots from Auckland side. This is how the Store config is via the GUI in Auckland. Look at the order as I want the Auckland site to be processed first followed by Sydney controllers.
On a recent customer project there was the need to migrate off of VDA TLS encryption and migrate the connections from StoreFront to Citrix Gateway.
The customer previously had StoreFront direct connections and used the VDA TLS encryption setup to provide a TLS encrypted session to the desktop or applications.
- As Citrix StoreFront delivers ‘anywhere -any device’ access, we put attention over the look and user experience with our Custom Citrix StoreFront receiver web interfaces. Your mobile/tablet users will get better user experience with our custom interface than the.
- Citrix Systems, Inc. Is an American multinational software company that provides server, application and desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies. Citrix products are claimed to be in use by over 400,000 clients worldwide, including 99% of the Fortune 100, and 98% of the Fortune 500.
- Remember, you need all of them in the chain. Continue reading and comment on the thread ‘Citrix Storefront and encounter certificate issue on IGEL OS’. Learn more, search the IGEL Knowledge Base.
The VDA TLS encryption setup was too much engineering labor for the day 2 day operations and therefore they asked for a alternate solution but still provide the client>desktop as an TLS encrypted session.
Storefront Server Citrix
Here we have two options, the first is to use Citrix Gateway and StoreFront as authentication but this introduces the users with a new logon screen and then delegates the credentials with json to StoreFront.
The second is forcing the connections from StoreFront through the Citrix Gateway by the means of optimal gateway routing, and we don’t have any user experience changes because the logon point is still StoreFront.
Citrix Workspace Download
Option two was chosen and after a quick and simple deployment a seamless migration with optimal gateway routing is in place.
All About Citrix Storefront Plugin


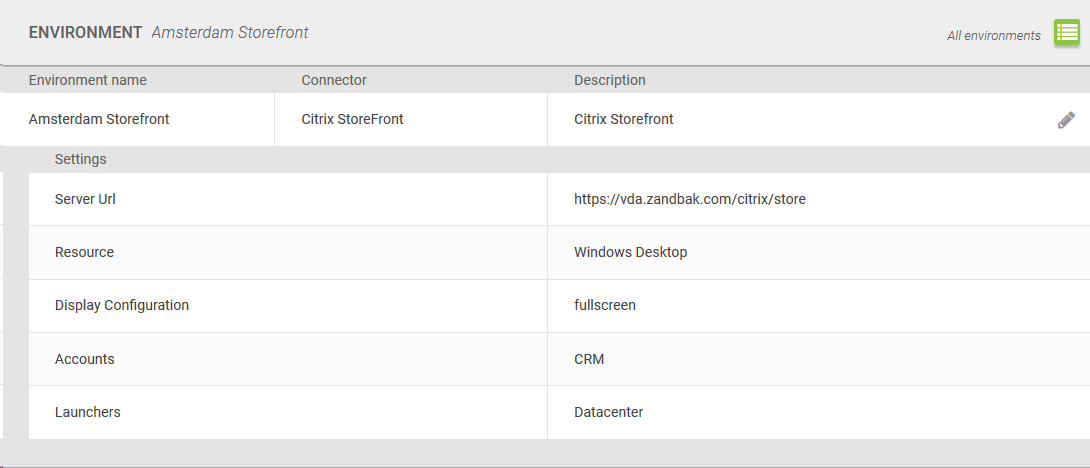
First all the preparation in place is creating a new Citrix Gateway DNS record and a new StoreFront load-balancer IP into the current setup will be migrated, afterwards configure the CVAD wizard on the NetScaler for a simple Citrix Gateway deployment and unbind any authentication policies because these will not be used. Afterwards configure all the necessary settings for a standard Citrix Gateway deployment and propagate these changes across the cluster. When all this is done edit the web.config file of the store that got configured under the primary StoreFront servers IIS inetpub directory and search for: optimalGatewayForFarmsCollection and make sure there is an entry with optimalGatewayForFarms enabledOnDirectAccess=”true” and save the file. Propagate the changes and after that migrate the old DNS entry to the new StoreFront ip. You will see that after logon the desktop brokering is force through Citrix Gateway.
The following reference articles where used for configuration and testing:
